These days the internet is awash with malware. You can never be certain that the file you just downloaded isn’t some malicious file pretending to be safe. In fact many malicious files are designed to do exactly this. This article will explain how to tell the difference between a safe file and a dangerous one. Although this may seem like a very daunting task, I do promise that it’s not too difficult. These days there are many very sophisticated, and simple, online services that allow you to make sure a file is not malicious. If you believe that the file is probably safe then make sure that you read section 1 first before you continue on. It may save you a lot of time.
Recent Changelog:
5/23/2014-Fixed dead links and added link to Best Free Antivirus Software article
6/9/2014-Replaced http links with https links wherever possible.
Index
1. Check If File Is In Comodo's Whitelist
2. Check File Using Comodo Valkyrie
A) Use Valkyrie To Find Out For Sure If File Is Safe
B) Alternatively Interpret Automatic Analysis Results Yourself
3. Check File Using VirusTotal
4. Check File For Malicious Behavior
A) Use Comodo Instant Malware Analysis
B) Use Anubis
1. Check If File Is In Comodo's Whitelist
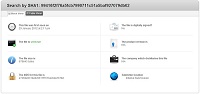
If you believe that the file in question is probably safe then it may not be necessary to go through the rest of the steps outlined in this article. First upload the file to Comodo Valkyrie. This is a free service provided by Comodo that allows users to upload files up to 20MB to be analyzed almost instantly. After uploading the file look at the upper left corner. There is a part that says "SHA1". Please copy the entire string of letters and numbers that are next to it. Now go to the page for Comodo File Intelligence.
We will be using this service to see if the file has already been verified to be safe and is already present in Comodo's huge whitelist of safe files. Once on that site change the search box from "Search by Filename" to "Search by SHA1". Then paste in the SHA1 and click "Search Now". Look at the information it provides. If it says that "The file is safe" then quickly look at the results from Comodo Valkyrie. If the Final Result from Comodo Valkyrie says that the file is Safe or Unknown then you can trust the file. You do not need to continue on to the rest of the steps. However, if Comodo Valkyrie says that the file is Malicious then you may want to continue to the second section to verify that the file is in fact not dangerous. It's almost certainly safe, but it shouldn't take too long to confirm that using a few more methods.
2. Check File Using Comodo Valkyrie
Comodo Valkyrie is a free service provided by Comodo that allows users to upload files up to 20MB to be analyzed almost instantly. This service can be found on this page. Just go to the site and browse to the file you're investigating. Then upload the file. These files will be checked by multiple types of detection including static detection, behavioral analysis, whether it is detected by Comodo Antivirus, and advanced heuristics.
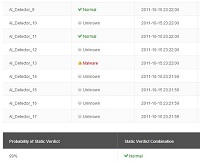
Using these detectors this service is able to provide a prediction as to whether the file is “Normal”, “Unknown”, or “Malicious”. A verdict of “Normal” means that the file is safe. “Malicious” means that it’s dangerous. If the analysis finds the file to be “Unknown” this means that it’s not sure.
Recently Comodo Valkyrie has been having problems where sometimes the page will not load, or if it does the analysis will never finish. It also works fine other times. Therefore, if this service does not work properly for you I would advise that you continue on to the next step in this article and continue the analysis.
A) Use Valkyrie To Find Out For Sure If File Is Safe
Also, some files may have already been manually analyzed by Comodo staff. If it has been analyzed the staff will have assigned it a verdict of Normal, Unknown, or Malicious. If they find it to be "Unknown" or "Malicious" then I'd advise getting rid of the file. I wouldn't trust it.
By the way, having them manually analyze a file is the only way to be absolutely certain that it’s safe. Thus if you want to be certain about the file, and it has not already been analyzed, you can manually submit the file to Comodo staff for analysis. To do this first make sure that you have an account with Comodo Valkyrie, and are signed in. If you don't already have an account, then it's very easy to get one. Simply go to "Sign Up", choose a UserName, give them a valid email address, and enter a password. I would highly advise that you create an account. After logging in you will see that at the top of the page it shows pictures of the analysts you can assign the file to. You can choose any analyst to investigate the file. It doesn't really matter which you choose.
After assigning the file they will manually analyze it and present you with the verdict. The possible verdicts are already explained above. This analysis should often take less than 24 hours. If you do decide to have the file manually analyzed then you don't need to worry about any other methods discussed in the rest of the article. Just submit the file and wait for the results. However, if you want to find out more about the file, and aren't willing to wait for the manual verdict, then the rest of this article should be very useful for you.
B) Alternatively Interpret Automatic Analysis Results Yourself
If you decide not to wait for the analysis then you can also use this service to quickly get a lot of information about the file. After the file is analyzed the most important parts to look at are the "Auto Result" and the "Final Result". Both results are given at the top of the page. The "Auto Result" will give you the overall result from the static detection". The "Final Result" combines the results from all types of detection to provide an overall prediction for the safety of the file. All services are discussed in greater detail below. If both of these give a verdict of normal then the file is likely safe. However, before looking at these overall results check the tabs for "Dynamic Detection and "Advanced Heuristics" tab to make sure that they have finished analyzing. This will take longer than the static detection. However, to get an even better idea if the file is truly safe then you will also want to look more closely at the individual results for each tab.
Note that for some files the result will read "No PE File". What this means is that the file does not contain enough information for Valkyrie to correctly run it. More information can be found on this page. Thus, if this is the result you receive I would recommend that you skip to the next section and continue to analyze the file using the alternate methods discussed in this article.
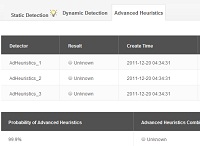
After the file is analyzed you will be presented with three different tabs of information. The first is called “Static Detection”. The tab shows the verdict of the 17 different AI detectors that checked the file. The individual verdict of these detectors is not important. Comodo uses a very sophisticated algorithm to determine the final verdict based on each of these detectors. What’s important is the overall result given at the bottom of the screen. This gives the automatic verdict in the box under where it says “Static Verdict Combination”. It also gives its confidence under “Probability of Static Verdict”.
The other tab we will be looking at is called “Advanced Heuristics”. This examines the file with more sensitive algorithms. These are more likely to catch malware but are also more likely to incorrectly identify a file as “Unknown” or “Malicious”. Please keep this in mind when interpreting these results.
3. Check File Using VirusTotal
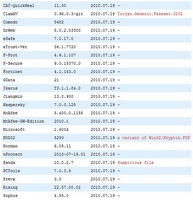
You can also find out whether any antiviruses (AV’s) detect it. One of the best services for this is VirusTotal. It can be found on this page. This service will scan any file you upload with over 40 different products and show the results separately for each one. You can upload files up to 64MB in size and the entire process should only take about a minute.
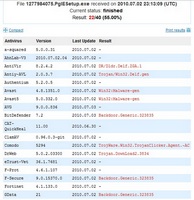
By far the most difficult part of using VirusTotal is interpreting the results. It can sometimes be difficult to tell from the results whether a file is likely to be dangerous. In general, if a significant number of scanners show a warning the file is likely to be dangerous. However, even if only a few detect it that does not necessarily mean that it is safe. Below are example findings for two files that are indeed malicious.
Using VirusTotal does have a few drawbacks. One of these is that it is certainly possible for malware to be so new that not a single antivirus yet detects it. I have personally seen this on multiple occasions. Thus, even if VirusTotal shows that no AV detects a file it does not mean that it is not dangerous. A related problem is that malware is being created so quickly that antivirus companies are forced to use heuristic detections and generic signatures in an attempt to keep up with it. The problem with this approach is that these detection methods may incorrectly identify a legitimate file as malicious. This is known as a false positive. These types of mistakes do occur, and with increasing frequency.
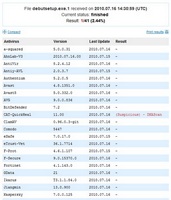
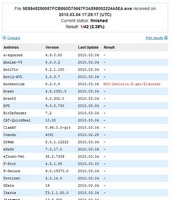
Thus, if only a few AV’s detect a file with heuristics, and the other AV’s do not, then this may be a false positive. However, this does not guarantee that it is. It's for reasons such as this that you should always check a file using all three methods discussed in this article. Below are example findings for legitimate files that are being incorrectly identified as dangerous by VirusTotal.
I want to be clear that even if only a single antivirus, or even none, detects a file as malicious then the file can still be dangerous. VirusTotal cannot be used to guarantee that a file is safe. However, if a very large number of antiviruses find the file to be malicious, then it likely is. This is the true strength of VirusTotal.
4. Check File For Malicious Behavior
In addition to the above methods you may also want to check the file for malicious behavior. There are many great services that can do this, but I have selected the two that I would most highly recommend. Do remember that legitimate files can be flagged as suspicious by them and that it’s also possible for malware to slip through undetected. In fact, some malware is even able to tell that it’s running in a virtual environment and thus refuse to run. It's for this reason, again, that it's best to use all three methods discussed in this article to analyze a file.
A) Use Comodo Instant Malware Analysis
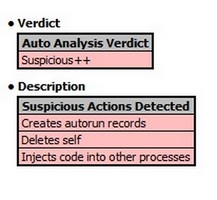
Comodo Instant Malware Analysis (CIMA) can be found on this page. I believe that the results of this service should be understandable by all users. You can upload files of any size to it and, after the upload is complete, it will immediately begin analyzing the file. The amount of time this takes is largely dependent on the size of the file and the complexity of its behavior. That said, in most cases it’s actually quite fast to analyze. I’d highly recommend using this service as it's very effective at recognizing suspicious behavior. Once the analysis is complete the results will be given at the end of the report.
The verdict may be “Suspicious”, “Suspicious+”, or “Suspicious++”. If the verdict is any of these this means that possibly malicious behavior was detected. It also gives the reasons it flagged it as such immediately below the verdict. “Suspicious++” indicates the most suspicious behavior.
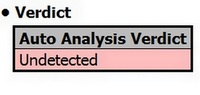
If it instead says that the “Auto Analysis Verdict” is “Undetected” then it did not find any suspicious activity. This doesn't guarantee that it's not dangerous, but it does make it more likely that it's not. Thus if the above steps didn't find any malicious behavior, and neither did CIMA, then you can be relatively certain that the file is safe.
More advanced users may also wish to use Anubis. This service can be found on this page. This is another highly effective behavioral analysis service. However, uploading files sometimes takes a very long time and the results are more difficult to interpret. That said, this service does provide a lot of information about the behavior of the file and will serve as a great second opinion to CIMA. If you're an advanced user I would highly recommend also checking the behavior of files with Anubis.
5. Report Dangerous Files
If your analysis shows that a particular file is dangerous I would recommend that you submit it to as many anti-malware vendors as possible. The easiest way to do this is to follow the advice I give in my article about How to Report Malware or False Positives to Multiple Antivirus Vendors. By following the steps outlined you can help prevent anyone else from being infected with that piece of malware.
Please help by rating this article. Also, if you believe this article deserves anything less than 5 stars, please leave a comment below explaining how you think it can be improved or where you find fault. This article is written by me but fueled by the community. Thus your opinions and advice are not only much appreciated, but actually necessary in order for this article to grow and improve.
If you found this article useful then perhaps you'd like to check out some of my others.
How to Clean An Infected Computer
How to Fix a Malware Infected Computer
How to Harden Your Browser Against Malware and Privacy Concerns
How to Install Comodo Firewall
How to Know If Your Computer Is Infected
How to Protect Your Online Privacy
How to Report Dangerous Websites
How to Report Malware or False Positives to Multiple Antivirus Vendors
How to Tell If A Website Is Dangerous
This software category is in need of an editor. If you would like to give something back to the freeware community by taking it over, check out this page for more details. You can then contact us from that page or by clicking here
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:

Comments
General Question about Comodo Autoruns Analysis. Even after closing and reopening Autoruns multiple times, there are a few files which Autoruns never finishes analyzing. I went ahead and assumed these files were FLS.unknown, and proceeded to check if they were malicious or not. Does this happen frequently?
I'm having trouble with 2 of the 3 files that came up as FLS.unknown in Comodo Autoruns. When uploading these two files to Valkyrie, it either just reloads the file upload page with a blank box, or, if I type the file address into the upload box, it comes up as a file error. I was able to run both files through www.virustotal.com and got the SHA1 text strings, and then searched Comodo file intelligence. One is unknown, the other is not in the database. I sent the latter to Comodo for further analysis as a suspicious file. Could malware be preventing this file from uploading? I used the Anubis analysis and received a report for one of the files, but since I'm not an advanced user, I have no idea what to look for to see if it's malicious or not. Any information would be great.
*** THIS IS A RESUBMISSION OF MY COMMENT YESTERDAY THAT MODERATORS DELETED DUE TO THE TYPO,'wwww' instead of 'www". PLEASE EXCUSE ANY CONFUSION MY ERRORS CAUSED. ***
Thanks again, Chiron, for an informative, well-written article from which I learned a lot.
The utilities I wish to share with fellow readers permit Context Menu uploads to VirusTotal. If the file's HASH exists in VirusTotal's DB, then results are displayed immediately; if not in the DB, then the file is uploaded for scanning.
NOTES:
A. The links take you directly to the file(s)-download, as I was instructed by Moderators. I think it would be a good idea to take a look at the respective websites' descriptions before downloading anything, especially as we are discussing security.
B. Like VirusTotal's own uploader, these utilities have a 32MB file-size limit unlike the 64MB VT web-browser limit.
They can be found here:
1. X-Ray: http://www.raymond.cc/blog/xray/ (Can use own API.)
2. Phrozen VirusTotalUploader: http://phrozenblog.com/?p=281.ps (Includes additional useful utilities.)
3. Virus Total Scanner: http://securityxploded.com/virus-total-scanner.php (Portable)
Except for my obvious, and easily corrected error of adding an extra "w" to an URL, I did exactly what you say I should do; i.e., provide a link to the tools' websites. On each link's landing page is PROMINENTLY displayed, in one case, the exact tool; and in the other case, a tab conspicuously labeled *TOOLS*.
Thank you for taking the time to correct any other "errors" I made in my (haha) "corrected" comment and not simply deleting it. Like yours and the other moderators' here, my time is limited and valueable and when I use it to contribute to this site, it would be nice to feel that fact is appreciated. If commenting in the future, I'll be more careful.
Regards.
I completely and totally understand and agree with you. In addition, since posting rules are there for me to have read and abided by, I ASSUME RESPONSIBILITY for not having read and conformed to them. Mea culpa, mea culpa, mea maxima culpa. :)
That being said, I still feel that before simply throwing away my sincere attempt to contribute, the same effort put into telling me it had been trashed in its entirety (accurate with the 'inaccurate')would have been put more usefully to correcting my simple errors.
A moderator took the time to follow my links, correct? When s/he found them to be errant, rather than spend the time emailing me about the error, would it not have been as easy and more productive to simply correct them rather that to "reprimand" me, a response to MY ERROR which benefited no one?
Of course, as you point out, you have the "power" to act dismissively and peremptorily toward, again as you point out, a regular visitor to this site but that is not the tone or atmosphere you wish to create, is it?
In any event, and ONCE AGAIN, should I post in future, I'll be more careful. I appreciate your engagement.
The file size that can be detected by VirusTotal.com has now been raised to 64 MB.
Hello!I am in a fix.my processors are working at 100 percent and no apps are running. I have scanned with MSE but no difference. I also cleaned the registry.its a win7 hp system.It started when I finished downloading files from kat.ph.the only other thing I remember doing is clicking on a popup on desktop that told me to check my hp warranty status.I also noticed that if taskmanager is running,the processors go back to normal operating levels..pls help me:(