 These days malicious software is becoming an epidemic. It seems like it’s everywhere. Also, sadly, there's been a change in the way malware acts. It used to be that it would slow down your computer, or display annoying popups, but now malware is becoming increasingly discreet. You could be infected right now and not even know it. Also, sadly, it often seems as if the only way to make sure you’re not infected is to scan your computer with numerous anti-malware programs. Doing this can be time consuming and, while scanning, may even slow your computer to a crawl. Even after that you still can’t be sure you're clean. This is because scanners cannot recognize all new malware.
These days malicious software is becoming an epidemic. It seems like it’s everywhere. Also, sadly, there's been a change in the way malware acts. It used to be that it would slow down your computer, or display annoying popups, but now malware is becoming increasingly discreet. You could be infected right now and not even know it. Also, sadly, it often seems as if the only way to make sure you’re not infected is to scan your computer with numerous anti-malware programs. Doing this can be time consuming and, while scanning, may even slow your computer to a crawl. Even after that you still can’t be sure you're clean. This is because scanners cannot recognize all new malware.
Because of these difficulties I have come up with a better method. This uses multiple programs, not to remove files, but just to analyze the computer. Each of these programs is very effective and easy to use. They are all portable applications and will not cause any conflicts on your computer because they are only running when you're using them. However, they do require an active internet connection to function properly. Don't worry, this guide will also help you to fix your internet connection in the event that it is not working. After you have already gone through the below process once, and had all files whitelisted, this approach is much faster, much more certain, and much easier than any other approach I've seen. No active malware can escape this process. However, inactive pieces of malware may not be flagged by this approach but may be found by other scanners. Rest assured that these are not direct threats to the safety of your computer and thus do not constitute a failure of this article.
This article is meant for those who believe it's possible, but are not sure, that malware is running on their computer. If you strongly believe that malware is running on your computer I would advise that you immediately reboot the computer into Safe Mode and follow the advice in this section of my article about How to Clean An Infected Computer. The reason I say that is that some malware will immediately start doing things such as encrypting files. Thus, the longer your computer is running in normal mode the greater the damage will be. However, if you only have fleeting suspicious that something may be amiss on your computer I recommend that you follow the below advice to find out for sure.
I also want to stress that in order to make sure that your computer is not infected you must follow each step. None is meant to be used independently. Each depends on the others to account for different infection scenarios. Also, if any step shows definite evidence of an infection you should move directly to the section which explains How To Clean Infections From Computer. There is no reason to continue your investigation if your computer is already found to be infected.
Recent Changelog:
5/23/2014-Fixed some links and added link to Best Free Antivirus Software article.
6/9/2014-Replaced http links with https links wherever possible.
Index
1. What To Do If Computer Is Unbootable
A) Use KillSwitch To Investigate Running Processes
C) Submit Unknown Files Which Are Probably Safe To Comodo For Whitelisting
A) Use Comodo Autoruns To Investigate Registry Entries
B) Analyze Comodo Autoruns Results
C) Submit Unknown Files Which Are Probably Safe To Comodo For Whitelisting
5. How To Clean Infections From Computer
1. What To Do If Computer Is Unbootable
Note that if your computer is able to boot into Windows you should skip directly to the next section. However, if your computer is not able to boot into Windows I would first advise that you follow the advice I give in this section of an article I wrote about How to Fix a Malware Infected Computer. It may be able to help make your computer bootable again. Then, once it's fixed, you can begin following the advice in the next section to see if your computer is infected.
Note that if the advice in that section of the other article is not able to fix your problems you should not follow part D in that article, but instead follow the advice given in this section of an article I wrote about How to Clean An Infected Computer. It's possible that the reason that your computer cannot boot is because of malware. Thus cleaning it may be the only way to get the computer running again.
2. Check for Rootkits
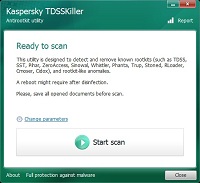
It's important to ensure that there are no active rootkits on your computer. To do this first scan your computer with Kaspersky TDSSKiller. It can be downloaded from this page. Note that if the executable version is not working correctly you should instead download the zip file containing the same scanner. At this same time download the zip file for Comodo Cleaning Essentials from this page. Make sure to select the correct version for your operating system. If you're not sure if your computer is running a 32 or 64 bit operating system then please see this FAQ. Note that if neither will not download correctly, or your internet connection is not working, you should download them on another computer and transfer them to the infected one via a flash drive. Make sure there were no other files on the flash drive. Be careful with the flash drive as the malware may actually infect it when you plug it into the computer. Thus, don't plug it into any other computers after transferring these programs.
Kaspersky TDSSKiller will scan your computer for some of the most common types of rootkits. I've found it to have relatively few false positives and a very high detection rate. By the way, some scanners, including Comodo Cleaning Essentials, may detect this file as a dangerous file. It is not. This is a safe download link. If it is flagged as dangerous you can safely ignore the detection. As with every program in this article, I recommend that you do not quarantine any files using this program. A false positive on the wrong file could destroy your computer, even if you’re not infected.
To use this it open the file called TDSSKiller. Then select the option to “Start Scan”. This scan should take less than a minute. If it does find anything then it's likely that your computer is infected. However, if you believe the detected files are not dangerous you can investigate them to see if they are false positives. However, if it does appear that the files are dangerous I would suggest that you skip to the last section of this article in order to deal with this infection. However, if it does not find any rootkit activity then you should next check your computer with Comodo Cleaning Essentials.
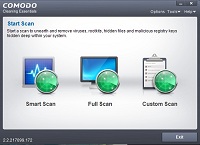
Now select the option to do a smart scan with CCE. It will immediately begin downloading the most recent virus database, which may take a long time to complete. Once it has completed downloading, the scan will begin immediately. This will scan your computer for all types of malware. The scan should not take too long to complete. As before, I recommend that you do not quarantine any files using this program. One problem with this program is that I do find it to have a few false positives. Thus the best option, in order to be sure of the results from its scan, is to report any files detected as dangerous, which you believe may be safe, to Comodo for analysis.
Sadly there is no easy way to navigate to the files detected by the scan. You will have to manually navigate to the path indicated in the scan results in order to get to them. Note that if you do not want to investigate them right now you can select the option to ignore each detection. Then allow finish and restart your computer. Next time you open CCE you can go to "Tools" and choose "Browse logs". The detections you chose to ignore, along with their file paths, should be stored in the most recent log. To report the detected files as false positives you should go to this page. Then select false positive, upload the files in question, fill out the required information, and select submit. Comodo analysts will send you an email with the results of their analysis.
This program also scans for system changes which may have been caused by malware. These will also be shown with the results. If you did not make these changes yourself then this could possibly be evidence that there is malware on your computer. I would recommend letting CCE fix these items, but not anything else, and continuing with the rest of the article to see if there is any more evidence of infection. I would not consider unwanted system modifications to be definitive evidence of an infection.
After the scan is complete it will ask you to restart your computer. Allow it to restart. Do not open any unnecessary programs as this will make the next step simpler. Once again I will remind you to not quarantine any files with this program. Once it restarts it will pop up with the final results. If it did not find anything, and neither did any of the above methods, then you can continue on to the next step. However, if it did find infections, and Comodo analysts also found them to be malicious, then I would advise that you skip to the last section in order to clean the infections.
Also, if your internet connection was not working please check again to see if it is now working. If not then you should go to this section of my guide about How to Fix a Malware Infected Computer and follow the advice given to fix your internet connection. A working internet connection is required for the remaining steps of this guide.
3. Use KillSwitch
A) Use KillSwitch To Investigate Running Processes
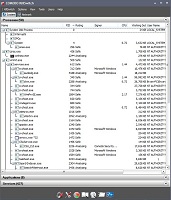
If the above steps did not find any malware activity then you should again open Comodo Cleaning Essentials (CCE). However, this time you should go to "Tools" and select the option to "Open KillSwitch". KillSwitch which will immediately begin analyzing all of your running processes. This analysis should only take a minute or so. Without waiting for the analysis to complete you can go to “View” and select “Hide Safe Processes”. This will hide all processes that are verified to be safe by Comodo. The reason I asked you not to open any other programs in the above step is because malware will nearly always run on system startup, while many legitimate programs will not. Thus there will be fewer processes to examine.
Once the analysis is complete all that are left are those programs which are either believed to be dangerous or are not in Comodo's whitelist. The latter type is denoted as FLS.Unknown. Be aware that unknown does not mean dangerous. It only means that the file has not yet been whitelisted by Comodo.
If KillSwitch now shows that “There are no items to show”, then your computer passed this part of the tests. You can move on to part 4. However, if there are files remaining in the list then you should investigate them. In order to do this you first need to navigate to the files. To do this right click on the process in question and select “Jump to Folder”. This will open up the folder where the associated file is located and select the file as well.
For files which are flagged as dangerous or suspicious, but which you believe may actually be safe, I would recommend that you report them as a false positive on this page. Just select false positive and fill out the required information. Comodo analysts will get back to you by email with the results of their analysis. In this way you can easily find out for sure if the files really are dangerous or not.
However, for those files which you think may be dangerous, but are only flagged as FLS.Unknown, you can check them yourself by following the methods discussed in my article about How to Tell if a File is Malicious. Also, if this verdict does in fact indicate that the files are likely safe, you can then submit them for addition to the Comodo Whitelist by following the advice given in part C.
For those files which are flagged as FLS.Unknown, but which you believe are probably safe, the most efficient way to analyze them is to submit them to Comodo for whitelisting. Instructions for how to submit programs, or individual files that belong to programs, can be found in this topic of the Comodo forum. Make sure you read through the first post entirely and follow all recommendations. This will ensure that your request is completed as quickly as possible. However, do note that in order to submit programs, or files, you do need to have an account on the Comodo forums. If you don't already have one then it's very easy to get one. There is an option to register on the top of any page on the Comodo forums. Also, if you cannot locate the folder indicated in the KillSwitch results that may be because some folders are hidden by default by Windows. To tell Windows to show you those folders please follow the advice on this page.
These submissions will be analyzed by Comodo staff and, if appropriate, added to the whitelist. However, do note that it may take the analysts days, or even a few weeks, to complete their analysis. This all depends on how many submissions they are also trying to analyze. If you feel that you cannot wait for their analysis then you also have the option of analyzing them manually by following the advice I give in How to Tell if a File is Malicious.
That said, the greatest advantage to the whitelisting approach is that you won't have to do any analysis of your own and the next time you check your computer the files will already be whitelisted and nothing will need to be done. In fact, you submit all the safe programs on your computer for whitelisting then, once they're whitelisted, the next time you scan with KillSwitch there should not be any more unknown processes for you to examine. Thus, it becomes an incredibly easy task to ensure that your computer is still clean of infections. In fact, my computer always shows a completely blank screen after selecting the option to “Hide Safe Processes”. This allows me to ensure that my system has passed this test in less than one minute. Please note that depending on your computer, and your internet connection speed, this time may vary. Once you're done with this part you can close KillSwitch.
4. Use Comodo Autoruns
A) Use Comodo Autoruns To Investigate Registry Entries
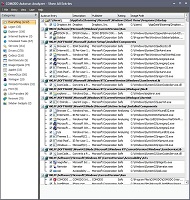
Now, through CCE, which should still be open, again go to the "Tools" menu. This time select the option to "Open Autorun Analyzer". This program will analyze the registry and show you the files associated with each item. Almost all malware will write to the registry. Thus, by scanning for all files associated with registry entries, this program can identify malware and unknown files, even if they aren't running. It may even be useful in identifying rootkits, although that is not its primary purpose. The downside to using this program is that it will potentially give you more files to check than the above methods. However, if you really want to be sure that your computer is clean then this step is also necessary. As before, do not delete/disable anything with this program as it can be very dangerous if used improperly. We are only using its analytical abilities. Please do not use it to try and clean up any infections or you could inadvertently harm your computer.
After Comodo Autoruns opens it will immediately begin compiling the list. This process could take a couple of minutes to complete. Without waiting for the list to finish being compiled you can go to “View” and select “Hide Safe Entries". Note that this option will now be pre-checked every subsequent time you run the program. Once the list is compiled Comodo Autoruns will automatically begin analyzing each entry. Wait until all entries have been analyzed. If this is the first time you have run this program, you should now close it and then open it again. I find that this often allows Comodo time to analyze some of the unknown files so that this time there will be less to check.
If Autoruns now shows that “There are no items to show” your computer passed this part of the tests. If it also passed all of the above steps then there is definitely no active malware on your computer.
If your computer passed all of the above steps, but you are experiencing problems with your computer, it's possible that the problem that you're experiencing is due to hardware or software issues. I would recommend that you first try searching online for symptoms similar to what your computer is suffering from to see if they match something other than malware. Also, an article I have written about How to Fix a Malware Infected Computer may be of use to you. It was written mainly to fix probelms due to malware, but the advice given should be able to fix many other types of software problems as well.
B) Analyze Comodo Autoruns Results
However, if there are still entries left over you should begin analyzing them. However, note that there is currently a minor bug with Comodo Autoruns. This sometimes causes the program to flag files which are actually known safe as FLS.Unknown. Thus, I would advise that if you see many files flagged as unknown, which you believe should be flagged as safe, that you close Comodo Autoruns and then open it again to see if the files are still unknown.
Also, note that you can make sure the virus database is fully up to date by always running a Smart Scan with CCE just before checking with Comodo Autoruns. This makes this problem much more rare. However, if you have previuosly run a Smart Scan and let the computer restart, and nothing was found, you do not need to have it restart just to make sure the virus database is fully updated. Just let the scan finish, and then, instead of letting it restart the computer, first close the results window without selecting any actions. Then right click on the CCE icon in the taskbar and choose exit. This will close the process and not allow it to restart your computer. You can then safely re-open CCE and use it to open Comodo Autoruns.
To get to the files which these entries are associated with, right click on an entry and select “Jump to Folder”. This will open up the folder where the associated file is located and select the file as well. Also, with this program you will find that often a single file has numerous entries, which means that often there’s not nearly as much analysis to be done as there would seem to be.
Just as was done for KillSwitch, for files which are flagged as dangerous or suspicious, but which you believe may actually be safe, I would recommend that you report them as a false positive on this page. Just select false positive and fill out the required information. Comodo analysts will get back to you by email with the results of their analysis. In this way you can easily find out for sure if the files really are dangerous or not. Also, if you cannot locate the folder indicated in the results that may be because some folders are hidden by default by Windows. To tell Windows to show you those folders please follow the advice on this page.
However, for those files which you think may be dangerous, but are only flagged as FLS.Unknown, you can also check them yourself by following the methods discussed in my article about How to Tell if a File is Malicious. Also, if this verdict does in fact indicate that the files are likely safe, you can then submit them for addition to the Comodo Whitelist by following the advice given in part C.
C) Submit Unknown Files Which Are Probably Safe To Comodo For Whitelisting
For those files which are flagged as FLS.Unknown, but which you believe are probably safe, the most efficient way to analyze them is to submit them to Comodo for whitelisting. Instructions for how to submit programs, or individual files that belong to programs, can be found in this topic of the Comodo forum. Make sure you read through the first post entirely and follow all recommendations. This will ensure that your request is completed as quickly as possible. However, do note that in order to submit programs, or files, you need to have an account on the Comodo forums. If you don't already have one then it's very easy to get one. There is an option to register on the top of any page on the Comodo forums. Also, if you cannot locate the folder indicated in the Autoruns results that may be because some folders are hidden by default by Windows. To tell Windows to show you those folders please follow the advice on this page.
These submissions will be analyzed by Comodo staff and, if appropriate, added to the whitelist. However, do note that it may take the analysts days, or even a few weeks, to complete their analysis. This all depends on how many submissions they are also trying to analyze. In addition, if you feel that you cannot wait for the analysis of Comodo staff then you also have the option of analyzing them manually by following the advice I give in How to Tell if a File is Malicious.
That said, the greatest advantage to the whitelisting approach is that you won't have to do any analysis of your own and the next time you check your computer the files will already be whitelisted and nothing will need to be done. In fact, you submit all the safe programs on your computer for whitelisting then, once they're whitelisted, the next time you scan with Comodo Autoruns there should not be any more unknown processes for you to examine. Thus, it becomes an incredibly easy task to ensure that your computer is still clean of infections. In fact, my computer always shows a completely blank screen after selecting the option to “Hide Safe Entries”. This allows me to ensure that my system has passed this test in just a few minutes. Please note that depending on your computer, and your internet connection speed, this time may vary.
5. How To Clean Infections From Computer
If any of these methods does show that your computer is infected you should check out my article about How to Clean An Infected Computer. The advice in this article will allow you to remove almost any infection and get your computer back to working order.
If you have any problems, or are confused by my directions, please leave a comment below and I will try to help. Trust me, if you are having a problem then so are many others. I need to know this so that I can improve the article and make it usable for everyone. Also, and this is especially important, if you find a situation in which none of these methods shows evidence of an infection, but the system is definitely infected, please let me know. I have seen no evidence of this happening, but if I do receive proof of a bypass then I will need to rethink my strategy.
In addition, please help by rating this article. If you believe this article deserves anything less than 5 stars, please leave a comment below explaining how you think it can be improved or where you find fault. This article is written by me but fueled by the community. Thus your opinions and advice are not only much appreciated, but actually necessary in order for this article to grow and improve.
If you found this article useful then perhaps you'd like to check out some of my others.
How to Clean An Infected Computer
How to Fix a Malware Infected Computer
How to Harden Your Browser Against Malware and Privacy Concerns
How to Install Comodo Firewall
How to Protect Your Online Privacy
How to Report Dangerous Websites
How to Report Malware or False Positives to Multiple Antivirus Vendors
How to Tell if a File is Malicious
How to Tell If A Website Is Dangerous
This software category is in need of an editor. If you would like to give something back to the freeware community by taking it over, check out this page for more details. You can then contact us from that page or by clicking here
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:

Comments
The link in the article for Comodo Cleaning Essentials leads to an old version from 2012. I am not sure if this is due to the article not being maintained or if that version is the preferred one.
The latest version is available from here (there is also some helpful information there)
https://help.comodo.com/topic-119-1-328-3523-Downloading-Comodo-Cleaning-Essentials.html
I can't access the files from CCE Autorun results. I can copy them but when I click on Jump to Folder all it will show me is the blue file which says application, not the path name I need to report for analysation. I also can't upload the files to the form to be analsyed for the same reason because when it says browse file, I can't find the file except on CCE Autorun. I wiould appreciate your help immensely. I feel kind of dumb because I have followed everything so far, and your article is excellent. Five starts, indeed! Thank you again.
Your email address has been removed as per our site rules for posting. Please post your query in our forum to receive assistance. MC - Site Manager.
http://www.techsupportalert.com/freeware-forum/general-computer-support/
Hi,
I am running Windows 10, and I looked up Comodo Cleaning Essentials (CCE) when checking my computer for infections. However, Comodo only lists CCE versions for Windows Vista, 7, and 8. Is there another program which will work like CCE for Windows 10?
Thanks, Karl
Hello, I hope this very, very interesting thread is still monitored.
I wonder if the dangerous infection analysis can be done on a system image backup on an external HDD hooked up to a known clean computer, rather than on the real thing which may be a mission-critical computer.
Thanks, G.
Hi,
I have no reason to believe my system is infected. TDSSKiller ran fine and found no threats. However, CCE does not work on my 64 bit system. It starts to scan and then just vanishes. This happens with any of the scan modes. It appears to be a problem as the forums at Comodo show this, but no fixes. You suggest to use Comodo Internet Security in another article, but I am leery as Comodo CCE fails and the chat failed at their website. I could not find a download page which may contain a more recent version of CCE. Not a great website. I understand you manage forums for Comodo. Can you help?
TIA,
Tom
Hello Chiron,
Thank you for such an easy to follow article on how to get rid of this vicious randsomeware virus we sadly have been infected with. I am NOT computer savvy, and had to download quite a few of your suggested software files and did so with ease.
I do believe after following your steps, that I have cleaned the computer. However, I say believe because our documents are all encrypted. This includes the word and excel as well as most of our pictures.
Does this mean we have lost all our documents and pictures? I'm very angry at myself, but the latest backup I have is from Dec 28, 2013. Is there an option I should be taking in Step #4, What To Do After All Malware Is Confirmed To Be Removed?
The computer is working fine and no threats have been detected. We just cannot open any files and I am hoping they are not all lost due to the attackers.
I would greatly appreciate your thoughts. Thank you.
Hey Chiron,
The articles are very well written and provided me with a lot of help, i am trying to get rid of malware. Thanks for you help.
One question though - while running the CCE or Kill switch you have said to "Without waiting for the analysis to complete you can go to “View” and select “Hide Safe Processes”. This will hide all processes that are verified to be safe by Comodo." but while running both programs the hide safe processes is unclicakble, therefore not being to understand what to do next.
Would help if you could let me know the next steps.
Thanks
yes you are correct it is grayed out.Comodo Autoruns works correctly.
do let me know what else needs to be done.
thanks
In "How to Know if Your Computer is Infected", section 4B, paragraph 1, you say that in order to reduce the occurrence of the bug in Autoruns where safe files are marked unknown, it is important to update the virus database by running a smart scan. Does this mean that every time I open CCE, I need to run a smart scan? Also, how would I skip past the screen where it asks me to fix system changes, which would then require a restart, and thus make the whole process useless? Do you see my point? How frequently does the virus database need to be updated?
It says that after running the CCE scan, to accept the restart prompt, and then after the restart that CCE should pop up again with the final results. I have been running all of these scans in safe mode w/ networking because I feared causing further damage (before I found your article, TrendMicro HouseCall found a Trojan, and I wasn't sure if it was gone or not). I'm assuming that going into safe mode is the reason that CCE does not pop back up after the restart. I assume this means that it does not finish the scan either. Can you explain what to do in this situation?
----Also, I read in the comments that most of these are best run when the computer is in Normal mode. Yet, earlier on in one of your articles you mentioned that if you suspect that your computer has malware, you should immediately boot into safe mode. Again, can you clarify what should be priority in this situation?
Hello there,
I downloaded Comodo like it was asked in the steps, unzipped it & then opened the file called "CCE".
As soon as it starts to download the updates, the windows suddenly freezes and the computer crashes then restarts, already checked it twice.
I don't know what to do in this case, please help.
TDSSKiller found a threat called sptd. I googled it and found out it is a driver of daemon tools which i have installed. So if TDSSKiller finds something it doesn't mean my computer is automatically infected?
Should I boot into safe mode before following your directions?
Thanks for your reply. I was getting ready to post again because I figured something out. You can select "ignore" from the scan results by clicking on "clean." If you do that the results will still show up in the log (linked under tools). I'm about to send those results to Comodo.
BTW most of my initial results were false positives, so you're right about that. I'd already run the quick scan and it came out clean. I was still concerned because I'd run a "complimentary scan" of another product that showed registry errors. That's why I ran the custom scan in both normal mode and safe mode. (I realize now it took so long because I didn't unselect the hard drives.)
I think these instructions need to be updated. When I didn't push "apply" after the Comodo scan was done, the results disappeared. They didn't appear again at the restart and they don't appear in the logs. I'm frustrated because it took hours to finish the custom scan I did and now I'll have to do it all over again. I remember where some of the files are, but not all of them. If I'd known they were just disappear, I could have written them down before closing the program.
I'm also wondering if it's as dangerous to quarantine files as to delete them. I had run an earlier scan before reading this article and did push "apply." That quarantined the files but didn't delete them. Is this a new feature of the program, or were you referring to quarantining files in your article?