These days it often feels like online privacy is an unattainable illusion. The truth is that there are many things you can do to greatly increase your privacy. This article is meant to present you with some general strategies to protect your online privacy. Please choose the methods that work best for you.
Also, you should be aware that protecting your online privacy also requires that you keep your computer safe from many other types of online dangers. Because of that I would also suggest that you read through my article about How to Stay Safe While Online.
Recent Changelog:
5/23/2014-Removed some dead links and added link to Best Free Antivirus Software article.
6/9/2014-Replaced http links with https links wherever possible.
Index
A) Make Sure Site Is Safe Before Sharing Information
B) Protect Your Wireless Connection From Dangers
C) Follow This Advice To Remove Your Information From Most People Search Databases
2. Increase Privacy Of Your Browser
3. Use A Privacy Oriented Email Service
4. Use a Virtual Private Network To Hide Your IP Address
5. Use Peerblock To Block Known Risks From Even Seeing Your Computer
6. Check Out This Site For Further Reading
1. Basic Strategies
A) Make Sure Site Is Safe Before Sharing Information
The truth about the internet is that often you can’t be sure who people really are or who's actually running the site you’re on. A general rule of thumb is that if you don’t trust the site don’t give them any personally identifiable information. This includes your real name, email address, credit card number, etc… To make sure the site you're considering visiting isn't a security or privacy risk you should read my article about How to Tell If A Website Is Dangerous.
B) Protect Your Wireless Connection From Dangers
Also, if you're connecting to the internet via a wireless connection you need to make sure that the connection is password protected. If possible use WPA type encryption, as this is very strong, and choose a password that would be very difficult for anyone else to guess. This will help prevent your browsing data from being spied on and, even more importantly, will help to protect your computer from being hacked. Once a hacker has breached your network defenses it becomes much easier for them to now try to get into your computer. Also, a further concern is that if you don't encrypt your wireless connection, and someone else uses it to do something illegal, it's possible for you to be held responsible for their actions.
C) Follow This Advice To Remove Your Information From Most People Search Databases
In addition, if you want to remove your information from most of the people search databases on the internet, you can follow the advice given on this page. The information on how to do this is actually provided by a company which offers to do it for you for a fee, but if you like you can also do it yourself for free. The problem is that it will take a good amount of time.
2. Increase Privacy Of Your Browser
Nearly all privacy threats enter your computer through your browser. Thus, protecting your browser from these privacy threats is a very important part of protecting your online privacy. To protect your browser from these types of threats please read the article I wrote about How to Harden Your Browser Against Malware and Privacy Concerns. Pay special attention to the parts which are concerned mainly with protecting your online privacy, but also remember that securing your computer against malware and other threats also plays a large role in protecting your privacy. Thus, I would really recommend that you read the entire article.
3. Use A Privacy Oriented Email Service
If privacy is really important to you then I would advise you to also consider using an email service which cares about privacy as much as you do. A very good list of free webmail services, which offer very good privacy, can be found on this page. Please read through it and figure out which email service is right for you.
However, if you instead need a service which can allow you to send emails anonymously, with no worries about receiving anything back, then there are some other services you should consider. For this sort of situation I would advise that you use either Send-Email or AnoneMail. Both are quite anonymous, although AnoneMail is slightly more anonymous. One aspect of AnoneMail is that it will even wait up to 12 hours to send the email, so it definitely can't be traced back to you. However, this may be too much of a disadvantage if you really want the other party to receive the email immediately.
4. Use a Virtual Private Network To Hide Your IP Address
A Virtual Private Network, or VPN, securely tunnels all of the connections from your computer to the secure servers of the service you are using. From there it is sent out to the site you're communicating with. However, the site sees only the IP address of the server, and has no idea what your real IP address is. Even better, because your connection is encrypted until it reaches their servers, nobody can spy on what you are doing. Thus, for the most part, nobody should be able to associate what you're doing with who you really are. Using a VPN is one of the most important steps in attaining true online privacy. Also, they are so easy to set up and use that anyone can use one.
In addition, some VPN's will allow you to choose servers which will make it appear that you are in a different country than you really are. This can help you to avoid censorship and even access content that may be restricted in your country. A review of some of the best free VPN’s can be found on this page.
For ordinary surfing my top recommendation would be SecurityKISS. This program does store your IP address, but this is only associated with the total amount of data sent tunneled through SecurityKISS. No other personally identifiable information is logged. Therefore I do not consider this to be a threat to your privacy. Also, this service does limit free users to 300MB of data per day. However, they do allow you to choose the country you would like to appear to be in. Sadly, SecurityKISS also does not work with torrents.
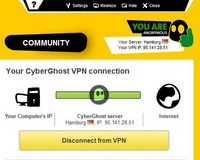
If you require a VPN which will also anonymize torrents you should check out CyberGhost. In fact, when compared with an un-anonymized connection, the torrent speed is not even slowed down significantly. This VPN does require registration, but you are not required to supply them with personally identifiable information. Also, this VPN only allows free users to use it to tunnel 1GB of information per month. That said, that amount should be sufficient for most users. Also, you cannot choose the country you would like to appear to be in.
A further restriction to this program is that free users can only use this service for 6 hours at a time before it will automatically disconnect. That said, the default action for this program is to block all internet connections in the case of a loss of connection. Thus, this should not be a large problem. Also, this service will not anonymize any emails sent via SMTP. Note that this service will anonymize https connections.
5. Use Peerblock To Prevent Known Risks From Even Seeing Your Computer
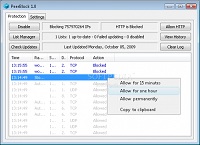
Peerblock can be downloaded from this site. It monitors all IP connections and blocks any connection which is in any of its lists of known unwanted IP addresses. It comes with default block lists and allows you to easily download more lists. It even comes with a list of known anti-P2P IP addresses, which you can select so that your computer will not communicate with them. All of these lists will be automatically updated each time you open the program. Additional lists can be found on this page. However, using this program does take a lot of getting used to. Thus I would really only recommend this program for advanced users.
You can also create custom lists, either for blocking or allowing sites. As long as you don’t use too many lists your connection speed shouldn’t decrease noticeably when it's enabled. Peerblock can greatly increase your level of privacy, but this comes at a price. Using certain lists may cause many of the sites you regularly visit to not work correctly. Thus, you will need to either temporarily disable Peerblock, when privacy concerns are not as critical, or create a whitelist of allowed sites.
Personally, I create a whitelist. The way I would recommend creating this is by first clearing the log. Then go to a site you visit regularly and see if important aspects of the site are blocked. If they are, and you trust the site, you can select the option to allow the connection for 15 minutes. I always start with the one at the bottom of the list. After temporarily allowing the single connection, and waiting for about 5 seconds, reload the page. If the site now loads fine then you can select the option to allow that connection permanently. This way the site will always work, even when Peerblock is active. Repeat this for each site you would like to whitelist.
6. Check Out This Site For Further Reading
Prism-Break is a site which is geared towards moderate to advanced users. The information provided on that site is comprehensive to the extent that the site claims that if you follow their advice you will be able to avoid data surveilance programs like Prism, XKeyscore, and Tempora. Advice, and links to programs, are provided for nearly all aspects of internet privacy. Thus, for those who are very serious about protecting your online privacy, I would strongly suggest that you check out that site. There is some very useful information provided. However, please be aware that I do not agree with all of their suggestions, and believe they have left some other very good alternatives out. Thus, I would recommend that you first follow the advice I give above. Also, before you decide to change the applications, and services, you currently use I would recommend that you first make sure that there is a problem with what you are currently using.
Please help by rating this article. Also, if you believe this article deserves anything less than 5 stars, please leave a comment below explaining how you think it can be improved or where you find fault. This article is written by me but fueled by the community. Thus your opinions and advice are not only much appreciated, but actually necessary in order for this article to grow and improve.
If you found this article useful then perhaps you'd like to check out some of my others.
How to Clean An Infected Computer
How to Fix a Malware Infected Computer
How to Harden Your Browser Against Malware and Privacy Concerns
How to Install Comodo Firewall
How to Know If Your Computer Is Infected
How to Report Dangerous Websites
How to Report Malware or False Positives to Multiple Antivirus Vendors
How to Tell if a File is Malicious
How to Tell If A Website Is Dangerous
This software category is in need of an editor. If you would like to give something back to the freeware community by taking it over, check out this page for more details. You can then contact us from that page or by clicking here
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:

Comments
The Peerblock product may be blocking obsolete or redundant IP addresses, in which case the product itself is of limited value.
I checked the source of its IP blocks from http://ipblocklist.com/ and attempted to access at least three dozen of the listed IP addresses. In almost every case, a message was returned: "The connection to [xx.xx.xx.xx] was interrupted" followed by a stock list of suggestions.
Try it yourself and see if you don't get the same result.
I read about SecurityKiss here and used it for about 6 months without any incident. Then one day it said I had to re-register to continue. Ok, I did, then a few weeks later it would show that I had used it for 23 hrs. when in reality I had just signed on. I don't understand it's behavior. Finally it just stopped working urging me to view the packages available that I could purchase to continue uninterrupted. I just uninstalled it getting nowhere. Now I kind of feel naked without my VPN shielding me.
Will try HotSpot shield hope this works indefinitely without incident. Excellent site by the way,, you guys have very detailed information and it's very explanatory. Keep up the great work! This is my "GO TO FIRST SITE" whenever I need anything.
The WalkingDead
way outdated article.
Hi
I'm coming back to the site after several months and I'm catching up the new site's rules just now.
Anyway, I decided to register to say "thank you a lot" for this great guide. Perfectly clear and easy to follow.
I've used it in my SOHO and I couldn't be happier.
Keep it up Gizmo's!
Sure, I'll do so. Thanks again!
Ratzo! "Hotspot Shield" is very secure, this VPN is safe and never keeps your log info in records. I am using it from 6 months and do not found any flaw in that. I suggest! you should always keep your public wifi usage with Hotspot Shield VPN.
For better online web privacy use only AnchorFree's Hotspot Shield free VPN without any hassle.