Introduction
With the amount of malware currently prowling the internet it's becoming increasingly important to protect your computer. Therefore I've separated my advice on how to stay safe online into two main sections. The first is the methods that I believe anyone from a novice to an expert user can use. The other section is aimed more at intermediate to advanced users. These methods may be more difficult to use, but your computer will be more secure.
Index
Security for Beginning to Intermediate Users
- Traditional Protection Layers (Antivirus, Firewall, HIPS)
- Protect Yourself Through Your Browser
- Use a Secure DNS Service
Security for Intermediate to Advanced Users
- Limit the Actions Malware Can Take
- Additional Browser Add-ons/Extensions
- Prevent Any Communication With Bad Sites
- Update Software and Encrypt Your Files
Security for Beginning to Intermediate Users
1. Traditional Protection Layers (Antivirus, Firewall, HIPS)
A. Protect your system from infection
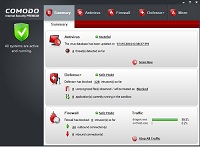 Installing an active antivirus program is one of the most important steps in keeping your computer secure. See this review of the Best Free Antivirus Software. All of the programs reviewed in that article scan for all types of malware, not just viruses. The problem with depending only on an antivirus to protect you is that no program can catch all malware.
Installing an active antivirus program is one of the most important steps in keeping your computer secure. See this review of the Best Free Antivirus Software. All of the programs reviewed in that article scan for all types of malware, not just viruses. The problem with depending only on an antivirus to protect you is that no program can catch all malware.
To compensate for that weakness I would advise that you also use a firewall with a built in HIPS component. See this review of the Best Free Firewall. Some of the firewalls reviewed have excellent security features, such as Comodo's new automatic sandboxing feature (using isolation) or Online Armor's "run safer" feature (using limited privileges). Personally, I would recommend Comodo Internet Security as it comes with an antivirus, firewall, HIPS, and an automatic sandbox. If you do choose to install Comodo Internet Security, or Comodo Firewall, here's my guide on How to Install Comodo Firewall. All HIPS programs require a little patience in setting up, and initially answering the warnings, but after that they're relatively easy to maintain. I would advise that you try one and see if you can deal with the alerts. If they're really too difficult for you then install a simple firewall that lacks a HIPS, but be aware that the protection offered is much less.
If you do decide to not use a proactive firewall, then a good alternative is to install a behavioral blocker, such as ThreatFire. These attempt to detect malware by its behavior, and should have significantly fewer popup alerts that a HIPS. Some malware is best detected by its behavior, so this is a potent second layer of active defense. However remember that just as with an antivirus, no program can detect all malware.
B. Scan for Existing Malware
If you want to ensure your computer is not infected, or perhaps you suspect it is, then I would advise scanning your computer with a few of the programs in this review. Also, run a scan with your current antivirus. The programs in the article are specialized scanners, but between them most malware will be detected.
After ensuring your computer is not infected it's now important to keep it that way. Part of doing that is to ensure that any files you download are not malicious before you run them. To learn how to do this you can read my guide on How to Tell if a File is Malicious. By following those methods, and using common sense, you should be able to avoid manually running any risky software. However, this still doesn't protect you from the files that attempt to run automatically.
2. Protect Yourself Through Your Browser
A. General Browser Protection
Almost all popular web browsers now provide some general protection. Firefox, Opera, Google Chrome, and Comodo Dragon have  encryption support (with SSL & TLS), deletion of private data, and popup blocking. They also produce warning screens to help you to avoid known malicious sites (anti-phishing, anti-malware protection). All of them also have private browsing modes that clear your tracks when you close the browser. Also, Chromium browsers, such as Google Chrome and Comodo Dragon, have built-in secure sandboxing. This makes them especially difficult for outsiders to exploit, even when hackers do find a bug. Comodo Dragon doesn't have the privacy concerns that come with Google Chrome. In addition it will warn you if the site you are visiting has a SSL certificate that may not be trustworthy.
encryption support (with SSL & TLS), deletion of private data, and popup blocking. They also produce warning screens to help you to avoid known malicious sites (anti-phishing, anti-malware protection). All of them also have private browsing modes that clear your tracks when you close the browser. Also, Chromium browsers, such as Google Chrome and Comodo Dragon, have built-in secure sandboxing. This makes them especially difficult for outsiders to exploit, even when hackers do find a bug. Comodo Dragon doesn't have the privacy concerns that come with Google Chrome. In addition it will warn you if the site you are visiting has a SSL certificate that may not be trustworthy.
For blocking tracking cookies I would advise that you enable the option to block third-party cookies in your browser. This will prevent sites from loading cookies that are not from the site you are currently on. Thus almost all tracking cookies will be blocked. The only time you may have problems, and need to disable this, is sometimes when a site redirects you to another page. That said, in most cases it will work fine.
B. Security Add-ons/Extensions
The website ratings freeware such as WOT, LinkExtend, and SiteAdvisor, and link scanners are reviewed on this page.
-
Web of Trust (WOT) (IE, Firefox, Opera, Google Chrome): With this installed if you happen upon a potentially dangerous site, WOT covers the screen with a warning and waits for you to decide whether to stay or leave. This is my favorite sort of approach since it leaves the final decision to the user. If you combine this with your own good sense in avoiding untrustworthy sites, then you have a solid and free web shield. Also, if you choose, you can ignore the WOT warning and go to the site anyway. You can even rate the site if you disagree with the current rating.
-
McAfee SiteAdvisor (IE, Firefox): This operates much the same as WOT. In addition it also has filtering features, which block links, and a search engine to help prevent unwanted, or potentially dangerous, sites from appearing in your search results. This problem with filtering becomes apparent when you consider false positives. If the filter draws from a false, or controversial, security rating for a site, then you won't even see the site in the search results to judge for yourself whether it is somewhere you want to go. However using it in that way is optional.
-
LinkExtend (Firefox): This scans links with eight online services and gives you the verdict of whether it is dangerous or not. Thus you are given the information, but the decision is still in your hands.
-
KeyScrambler (IE, Firefox): This encrypts your key strokes so that even if you have a keylogger on your computer your passwords, and personal information, will be protected. If you have a good HIPS installed this shouldn't be necessary.
-
LastPass (IE, Firefox, Google Chrome, Comodo Dragon): This is an effective password manager, with automatic password and form filling. It not only helps protect your passwords, and sensitive data, but also allows you to confidently create strong pass
 words and change them often.
words and change them often. - Adblock Plus (Firefox): This allows you to subscribe to many different filter lists, which help block unwanted or malicious content. This can include malware domains or unwanted privacy threats (tracking, web bugs, and marketing-analysis strings). You can subscribe to any of the lists on that page, but be aware that subscribing to too many will slow down your browsing experience. I'd advise subscribing to either Fanboy's List or both EasyList and EasyPrivacy. In addition it may be a good idea to subscribe to Malware Domains.
-
AdThwart (Google Chrome, Comodo Dragon): This serves the same purpose as Adblock Plus, except it works on Chromium browsers. You can even use the same filter lists.
-
AdBlock (Google Chrome, Comodo Dragon): This is an alternative to AdThwart.
3. Use a Secure DNS Service
There are many good free DNS providers currently available. They are relatively easy to setup and require no software. These services use servers that are more secure than your regular ISP, and they even filter out any known malicious content before it ever reaches your computer. If you want to understand the technical details about how they work you can read about them here: IP Addresses Explained, DNS Primer.
Below I have listed three of the best services currently available. Just choose the one that best fits your needs. None of them will slow down your connection. In fact, you may even notice an increase in speed. Each of these has malware blocking capabilities, but at the moment it appears that Norton DNS and ClearCloud DNS are much more potent at preventing malicious downloads than Comodo Secure DNS. Hopefully Comodo Secure DNS will improve as the service matures. I have listed the server names you will use to set up the DNS servers below, but if you're not sure how to set them up you can follow the directions provided by the service on its page.
|
|
Security for Intermediate to Advanced Users
The methods discussed here may take more work to setup and manage, but if you're willing to put up with the extra hassle they will also provide you with superior security. Be aware that these are in addition to those methods already discussed above. Therefore, if you haven't already read through the simpler methods then please go back. Otherwise, read on.
1. Limit the Actions Malware Can Take
A. Use Least-privileged User Accounts (LUA)
If you're not running a strong HIPS program then I highly suggest that you use a limited/standard user account (LUA or least-privileged user account) instead of a normal administrator account. Running your computer in a LUA should be able to protect you from the majority of malware. This is essentially what User Account Control (UAC) is in Windows Vista and Windows 7. However, you will have to answer alerts for many of your programs in order to get them to work. If you want to use UAC, but don't like the alerts, you can use TweakUAC. This has an option to run UAC in "quiet mode". In this mode UAC will not display the elevation alerts. For information about whether this makes your system less secure you should read this article.
If you're running Windows XP then I would suggest you download DropMyRights. This will allow you to selectively reduce rights for particular applications. However you will have to manually create, or modify, shortcuts. Also, XP users who are running their computers in a LUA may want to use SuRun to run some applications with more privileges.
B. Isolate Malware From Your System
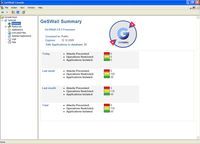 You can improve your online protection further by isolating, or sandboxing, applications that frequently use the Internet. Thus the vast majority of malware cannot get a foothold on your system. If you are willing to put up with the slight learning curve of Sandboxie, or GeSWall, then I highly recommend that you use one of those products. Personally I like Sandboxie, but use whichever best fits your needs. Both programs are reviewed in this article about the Best Free Protection Utility. Each program should be able to protect you from infection, even if the malware is zero-day and not detected by any scanner.
You can improve your online protection further by isolating, or sandboxing, applications that frequently use the Internet. Thus the vast majority of malware cannot get a foothold on your system. If you are willing to put up with the slight learning curve of Sandboxie, or GeSWall, then I highly recommend that you use one of those products. Personally I like Sandboxie, but use whichever best fits your needs. Both programs are reviewed in this article about the Best Free Protection Utility. Each program should be able to protect you from infection, even if the malware is zero-day and not detected by any scanner.
A general approach to using the methods discussed in this section is given in this article about How to Surf More Securely.
2. Additional Browser Add-ons/Extensions
-
NoScript(Firefox): This addon will block nearly all scr
 ipts, and other possibly dangerous content, from executing. This means that even if you stumble onto a dangerous site you cannot be attacked unless you manually add the scripts on that site to your whitelist. Thus you are protected from harmful scripts and many privacy threats. However, many sites use such scripts, and plugins, for legitimate purposes. These sites will not work correctly unless you manually add the scripts on that site to your whitelist. You can also configure it to block web bugs to help protect your privacy. For this go to "Options > Advanced > Untrusted" and forbid web bugs. Using NoScript takes some getting used to, but if you are serious about staying safe online this addon is a must have.
ipts, and other possibly dangerous content, from executing. This means that even if you stumble onto a dangerous site you cannot be attacked unless you manually add the scripts on that site to your whitelist. Thus you are protected from harmful scripts and many privacy threats. However, many sites use such scripts, and plugins, for legitimate purposes. These sites will not work correctly unless you manually add the scripts on that site to your whitelist. You can also configure it to block web bugs to help protect your privacy. For this go to "Options > Advanced > Untrusted" and forbid web bugs. Using NoScript takes some getting used to, but if you are serious about staying safe online this addon is a must have. -
NotScripts(Google Chrome, Comodo Dragon): This provides much of the same protection for chromium browsers as NoScript provides for Firefox.
-
CS Lite(Firefox): This addon extends your privacy protection by allowing you to block all cookies by default. CS Lite allows you to quickly allow/block cookies globally and then manually add exceptions for individual sites. Like NoScript this takes some getting used to, since many sites will not work correctly without cookies, but if protecting your privacy is important then this is another must have.
-
Vanilla(Google Chrome): This is a cookie manager for Google Chrome. Unlike CS Lite it doesn't block cookies automatically, but in the options you can select to "Auto delete unwanted cookies after 30 minutes". I would suggest enabling this feature. You can also configure it to clear unwanted cookies on startup. Just as with CS Lite you have the option to add the site you're on to your whitelist. This is a great extension to get if you use Google Chrome.
3. Prevent Any Communication With Bad Sites
There are many free programs that allow you to block bad sites based on a site's IP address. The very best type of IP Blocker that I've tried is PeerBlock. It's a very simple program that monitors IP connections and blocks connections that are on one of its lists of bad, or unwanted, sites. It comes with default block lists and allows you to easily download others. You can also create custom ones. PeerBlock will automatically update the lists for you. As long as you don't subscribe to too many lists it also uses very few resources. It even provides privacy protection for P2P users. You can read more about the program on this page.
In addition to this I would advise using hpHosts, Hostsfile, or MVPS Hosts. Thes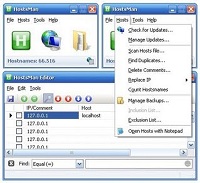 e not only focus on preventing malicious content, but also help reduce ads. However, they do not provide any protection for P2P users. All of these Host providers frequently update their block lists, but you will have to manually download them on a regular schedule (perhaps monthly). Choose only one of the three if you manage them on your own. However, you can use HostsMan to quickly update host files like hpHosts and MVPS Hosts. You can even download both of them, combine them together into a single Host file, and automatically optimize them by deleting duplicate entries. MVPS highly recommends setting the default update method to "overwrite current Hosts file", since it will prevent old entries from remaining in the file. Note that there is always a possibility that malware may try to worm its way into the file. For this reason some programs lock the Hosts file. WinPatrol, and most proactive firewalls (Comodo, Online Armor, etc.) will also detect attempts to access or change it. Also, users with Windows Vista, or Windows 7, may have to shut their DNS client service down to avoid slowdowns. All of the host providers above give directions on how to do this. I haven't noticed connection slowdowns with the filter lists I've tried.
e not only focus on preventing malicious content, but also help reduce ads. However, they do not provide any protection for P2P users. All of these Host providers frequently update their block lists, but you will have to manually download them on a regular schedule (perhaps monthly). Choose only one of the three if you manage them on your own. However, you can use HostsMan to quickly update host files like hpHosts and MVPS Hosts. You can even download both of them, combine them together into a single Host file, and automatically optimize them by deleting duplicate entries. MVPS highly recommends setting the default update method to "overwrite current Hosts file", since it will prevent old entries from remaining in the file. Note that there is always a possibility that malware may try to worm its way into the file. For this reason some programs lock the Hosts file. WinPatrol, and most proactive firewalls (Comodo, Online Armor, etc.) will also detect attempts to access or change it. Also, users with Windows Vista, or Windows 7, may have to shut their DNS client service down to avoid slowdowns. All of the host providers above give directions on how to do this. I haven't noticed connection slowdowns with the filter lists I've tried.
If you use too many of these lists, such as a large hosts file and many IP blocklists, then they may slowdown your connection speed. Choose them wisely. One idea is to get just a few at first, and then later decide whether you want more filtering. It's important to get to know what they do, and learn which list blocks which content. This way you can build the protection that best suits you.
4. Update Software and Encrypt Your Files
A. Repair Security Holes in your Software
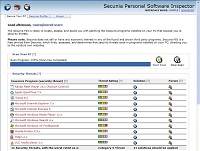 Secunia PSI will scan your computer for programs that need to be updated, or are end of life. This way if one of the programs you use has a known vulnerability you will be alerted so you can update it. Secunia PSI provides you with helpful links to update software as well as a rating of how critical the vulnerability is. However, it automatically adds itself to the task scheduler, without asking, and is generally slow. For regular updating please see this article on Software Update Monitors. That said, Secunia is a well respected source of information. If you like you can search its site to read about possible security threats and vulnerabilities before determining the trustworthiness of an application.
Secunia PSI will scan your computer for programs that need to be updated, or are end of life. This way if one of the programs you use has a known vulnerability you will be alerted so you can update it. Secunia PSI provides you with helpful links to update software as well as a rating of how critical the vulnerability is. However, it automatically adds itself to the task scheduler, without asking, and is generally slow. For regular updating please see this article on Software Update Monitors. That said, Secunia is a well respected source of information. If you like you can search its site to read about possible security threats and vulnerabilities before determining the trustworthiness of an application.
B. Cloak Your Sensitive Information
Encryption is a good way to protect your personal information from prying eyes, and malware. In this way even if malware gets through your defenses, and starts scanning for sensitive data, it won't be able to do any harm. Before you use encryption you need to understand the pros and cons. As a start you should read this article that discusses why Encryption is Not Enough.
Tags: prevention based computer security, least privileged user account methods, isolation/sandboxing, security addons/extensions, NoScript, CS Lite, secure DNS, Secunia PSI, Virus Total, WOT, PeerBlock/Host files, hpHosts/MVPS/HostMan, Adblock Plus, website blocking, content filtering
This category is maintained by volunteer editor Rizar.
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:
