I was asked by a colleague to write an article on light virtualization. While this kind of software is not my forte, I spent some time studying the market and testing various programs that offer the relevant functionality. This article should be a good starting point for anyone interested in an additional dimension of software, mostly useful for testing and security.
Today, I will give you a brief overview what light virtualization really means and what it offers, compare it to several alternatives, discuss the general pros and cons, as well as introduce a number of programs. We will focus on two types of light-virtualization programs: instant-snapshot-and-rollback programs and sandboxing tools.
What is light virtualization?
As the name implies, this kind of software involves some sort of an abstraction layer between your operating system and the higher application stack. Unlike full virtualization, where you can have fully encapsulated operating systems running on top of the host machine, light virtualization relies on your existing system to function. In other words, your system is an integral part of the solution. This means that you cannot port your setup between computers. However, light virtualization still offers more portability than a static setup, because you do have the ability to rollback changes to your system.
How does this work?
Light virtualization software uses drivers that intercept disk traffic and write changes to a temporary buffer. If committed, this buffer becomes a snapshot. If discarded, all changes done to your system are gone, as if they never happened. In a way, you can treat light virtualization as a mechanism that turns your underlying system or the portions under the control of the software into a read-only baseline and then builds layers of changes on top. If you like the changes, you can commit them, if not, you delete them.
How is this different from system imaging?
Full system imaging is very similar to light virtualization. However, some notable differences exist. Full system imaging is an all or nothing solution; you snapshot your entire system and then roll back all changes. Light virtualization programs normally allow you to monitor specific portions of your system, increasing your operational flexibility. Other useful features include the control of processes and data.
What is it good for?
Some people will say security. Personally, I believe that light virtualization is mostly useful for testing software in the native environment. This is particularly true for programs that require 3D acceleration, which will not be available in full virtualization. Moreover, in some cases, light virtualization may allow you to continue working without reboots or disruptions to your production setup. Security does play a secondary part, as you could use this kind of software to revert unwanted changes to your system or programs, but the correct use requires discipline and skill.
A combination of full virtualization and light virtualization, as well as system imaging and data backups can offer an extremely robust and flexible setup for advanced users, beta testers and software researchers. For example, you may want to run other operating systems as guests in your virtual machines, test new browser features inside a sandbox, revert registry changes following an undesired upgrade, as well as periodically save your system state in a full image.
What is it not good for?
Light virtualization is a parallel solution to the data and system image backup and the virtualization stack. In practice, you can easily get away without using light virtualization. You can multi-boot, use dedicated hardware for testing, use virtual machines for your specific work or corner cases and maintain system security by using vendor-provided security solutions like EMET. Light virtualization should not be treated as a silver bullet against malware, mistakes or neglect. Light virtualization will benefit users only when they are fully aware of their actions and with a solid backup plan in place.
Types of light virtualization software
There are two main types of light virtualization software.
One, full-system snapshot-and-restore programs that are almost identical to system imaging, except that you have the ability to monitor only specific parts of your system. Moreover, these kinds of programs will normally freeze your system state, allowing you to run in a virtual read-only mode, similar to working with a Linux live CD. Some of these applications will allow you to preserve your changes at the end of the day by unfreezing monitored programs or sections of the system. Again, to use the Linux analogy, this is similar to live CD persistence.
Two, sandboxing programs that allow you to freeze specific programs and/or isolate them into virtual containers that disallow access to the rest of the system. These programs force sandboxed processes to live with limited disk and memory access. Should violations occur, either deliberate or accidental, they will be contained inside the sandbox or even blocked from executing in the first place. Again, for the sake of convenience, many sandboxing programs will allow you to preserve the temporary buffer between sessions by committing changes to the disk. However, this should be done at the discretion of the user, as it is possible to preserve bad content along with the desired data.
We will now examine a small number of free programs, including a brief overview of their features, the ease of installation and use, the level of intrusiveness, convenience, flexibility, as well as the optimal use cases.
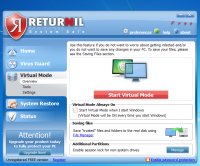
Returnil System Safe 2011
Returnil System Safe is advertised as an advanced anti-malware and virtualization technology. Several versions are available, with the free edition intended only for non-commercial and home use. The program has many features, including a real-time anti-malware and anti-spyware engine, a system restore management facility and the virtual mode, which lets you use your mode in the test-and-discard fashion.
The installation is quick, however the program has known compatibility issues with Windows 8 Developer Preview Edition. Overall, it is fairly simple to navigate, but the interface is rigid and non-resizable and uses its own theme. In my testing, the program worked well, although I did not test the anti-malware component, as I find it completely unnecessary.
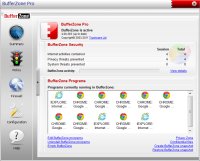
TrustWare BufferZone Pro
BufferZone is a sandboxing solution you can use to create virtual zones for your Internet facing applications. This way, you can prevent errors that may occur in your software, plugins or extensions, whether as a result of bad coding, bugs or possible rogue activities and misuse, from carrying over into your system. BufferZone offers a similar functionality to Microsoft EMET. You can run programs inside and outside zones and create program snapshots. The program installs cleanly and is very easy to use. Sandboxed programs are marked by a red rectangle around the window border.
Sandboxie
As the name implies, Sandboxie is a sandboxing solution for Windows, allowing you to run applications in an isolated space. The main focus of the program is on security, allowing users to browse the web securely, while enjoying privacy and protection against known and unknown vulnerability exploits in software. Sandboxie can also be useful for testing program changes and new features for existing applications.
For example, you might be interested in trying out browser addons or new media plugins and codecs. The program is very simple to install and use, although it does not yet work with Windows 8. You also get plenty of interactive help while using Sandboxie, which new users will definitely appreciate. Sandboxie paints window borders in yellow to distinguish them from regular, non-sandboxed instances.
Other solutions
This article cannot possibly cover all available programs, especially since many cost money and offer only limited free trials. However, you might also want to consider Microsoft EMET, a general-use toolkit that can help isolate applications from breaking out of their memory space and possibly damaging the rest of the system. The big advantage of EMET is the seamless, native integration with the system and zero performance overhead. However, Microsoft EMET is not a light virtualization technology per se, although it uses some of the same mechanisms employed by sandboxing software. It is definitely worth examining and testing.
Conclusion
This article should get you started with light virtualization. It elaborates on the principles of light virtualization, differences compared to full virtualization and system imaging, and recommended use cases. You also have one full-system snapshot and rollback program and two sandboxing applications to begin your exploration and testing.
It is important to remember that light virtualization does not replace other important elements of your data and system integrity strategy, including verifiable periodic backups, caution when working with online content and general common sense. Light virtualization should be treated as a flexibility addon to an existing and already robust setup characterized by lots of frequent changes and testing. Security can also be incorporated as an additional benefit. However, from the security perspective, neither offers any significant advantages over Microsoft's EMET or dedicated virtual machines.
To wrap it up, light virtualization is a useful if less known application category probably best used for software beta testing, although skilled, advanced users will find security merits, too. You are welcome to disagree, of course. Well, that would be all.
Cheers,
Dedoimedo
About the author:
Igor Ljubuncic aka Dedoimedo is the guy behind dedoimedo.com. He makes a living out of his very hobby - Linux, and holds a bunch of certifications that make a nice pile in the bottom drawer.
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:
