Following some of the recent security-related postings here, some of you have asked how best to choose a strong (ie, uncrackable) password.
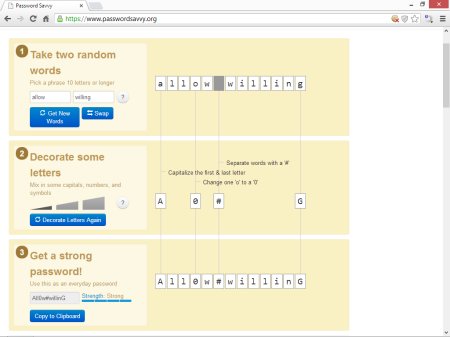
My advice has always been to choose 2 unrelated words, separated with a non-alphabetical character. If you read the item about how password crackers work (http://www.techsupportalert.com/content/want-find-out-how-password-cracking-works.htm) you'll know all about hashes. One characteristic of a hash is that you can't crack a small part of a hash. It's all or nothing. So if your password is "allow2willing", for example, cracking each word in turn simply won't work. The cracker has to be lucky enough to guess both words, plus the separator.
For added strength, you can tweak some of the letters in one or both of the words. Perhaps change some of the L's to 1's, or some of the O's to 0's etc.
If you need inspiration when a web site asks you to choose a password, try opening another browser tab and going to www.passwordsavvy.org. This site walks you through the process of creating a random, strong password, and then copies it to the Windows clipboard ready for you to paste into the other site.
As to how you subsequently remember that strong password without writing it down, I'll leave for tomorrow!
 We are looking for people with skills or interest in the following areas:
We are looking for people with skills or interest in the following areas:

Comments
I wonder how a dictionary attack would work against a password that's a combination of Flemish, Malagasy, Latin and Hawaiian words?
It simply wouldn't. That's why it is a great way of creating a strong password
The method I employ and recommend to my customers uses keyboard sequences, instead of the typical tired suggestion. By using keys which appear together, you can have ridiculously long passwords that are seemingly random, yet are easy to recall, don't spell or use words and can even be extended to give you ample choices in terms of how long it needs to be, passwords for certain sites do need to be as long or complex as your banking password.
for instance, you could have qweLKJ234 for a social networking site
and qweLKJ234234000 for your banking.
and easy to remember!
Good Luck!
That's fine if you only have a small number of logins. I'd have probably 150 or more. I'd suspect that most internet users would have in the region of 25+ which would make it rather difficult to remember all those different logins using a baseline like you have. However, if it works for you fine, not criticising, but I would suspect it is not that helpful for most internet users.
Infinite Password Generator 3.1 has a 128 character length limit.
Thanks for flagging up Infinite Password Generator (IPG). This is very topical for me at the moment as I am trying to find a convenient but powerful way to secure the use of Keepass. Just a few points tho'. I note below that not many have added the use of a key file as a further mechanism to secure access - is that not a consideration? I am playing with IPG; am I right in assuming that the particular instance of IPG that I am using will generate a unique password string for me based on my key phrase? For example if someone else gets my key phrase then can they generate the same p/w from their version of IPG? I am also bothered by key logging grabbing my key phrase - how can that be stopped with IPG as I see that keyscrambler - which I use - doesn't work with IPG? I'm a novice as my username suggests.
Thanks for the information. I didn't know about Infinite Password Generator and I will try it out, I don't use passwords longer than 16 characters so Keymaker20 still suits me, but I like learning about new programs.
Something else I like about Keymaker though is that it is not installed.
I refer to Message 107523. I agree with charlieb.za about using Keymaker20 as a good way to generate the same complex master password for a password manager. Unfortunately, Keymaker20 has a length limit of 16 characters, which might be too short for some of you paranoid people.
I have found another password generator that functions must like Keymaker20. It's called Infinite Password Generator 3.1. Here's the link:
http://www.ikitek.com/products/Infinite-Password-Generator.html
I have another suggestion which may be helpful.
I use KeePass to store all my passwords in so that I don't have to remember them. The weak point is then my KeePass password and I would probably not remember a strong one so I use a small program called Keymaker20. After setting up how long you want the password to be and whether you want capitals, numbers and special characters (@ # $ etc) included all you have to remember is a simple word or phrase which the program converts to a complex password, which I then use to open my Keepass database.
Actually, the password chosen ("allow2willing") is pretty vulnerable to a dictionary attack. Both "allow" and "willing" show up in this list of the 5000 most common English words: http://www.englishclub.com/vocabulary/common-words-5000.htm. I think that if someone was trying to brute force your password that they would probably fairly early try a pattern of 'common word''number''common word'. Even if they tested with a 100,000 word list, they could try all of the possible combinations (1 x 10^11) in a short period of time (if they can generate 10,000,000 hashes/second, it would take less than 3 hours).
Also, I don't recommend making simple substitutions like 1 for l or 0 for o. Crackers are aware of these substitutions, and so they will also show up in any dictionary used.
Far better is to make unusual substitutions. For example, substitute 3 for o, or t for e. As long as you don't inadvertently make an existing word or split your word into two words that exist in the dictionary, making a substitution like this will add to the computational complexity of the password while not adding much to how hard it is to remember. Another easy way to add complexity is to capitalize one or more letters in the middle of words.
Personally, I use KeePass for my passwords and Diceware to choose passphrases.
>> Also, I don't recommend making simple substitutions like 1 for l or 0 for o.
>> Crackers are aware of these substitutions, and so they will also show up in any dictionary used.
I already made that remark several times in comments, but apparently no article editors pay attention to it or are willing to accept the truth...
It's frustrating that too many sites (including banks, which really need to promote strong passwords) refuse to allow any special characters and limit you to alpha-numeric passwords only.
Yeah, totally agree. My main bank won't allow any non alpha/numeric characters or spaces. Well DUH! Talk about limiting complexity!
Gosh, I even have a bank which doesn't have a third tier authentication. All I have to do is enter a username and password. FFS!!!! AND, it won't accept capitals or, surprise surprise, non alpha/numeric characters.
My main bank Requires that I use the card access number printed on the card, password and then the final tier which is entering numbers or characters from another card which has a cross referenced grid, i.e. grid reference B 5 might be 4, C 6 might be H and so on. Have to get all 3 or it bombs out.
Unfortunately, I have the same experience.
My ISP eg. forces me to use a six (yes only 6!) characters long password.
For my bank websites I'm rather confident: they're websites don't use name/password, but a number generated by a piece of hardware where I have to
- put in my bank card,
- type in my pincode and
- the number shown on the website.
That seems quite unbeatable to me.
If somebody knows your bank card number/name sequence that you have to put in, and also finds out your pin code, then you're stuffed. Putting the final bit on the screen to type in. OMG, here that noise... sounds like big bruvver is coming to steal all your money.
>> If somebody knows your bank card number/name sequence that you have to put in
>> and also finds out your pin code then you're stuffed.
No I'm not. You need the physical bank card to put in the little card terminal (the hardware I was referring to)
But if someone has your bank card AND knows the pin code, you're ALWAYS stuffed. Also in real life.
Are you saying that you have a device that attaches to your computer into which you have to insert your card? If so, what a hassle if you don't have it on you. Sounds like a great way to turn people off internet banking.
>> Are you saying that you have a device that attaches to your computer into which you have to insert your card?
I have a device into which I have to insert my card indeed.
But it is NOT attached to my computer. It's a stand alone device I received from my bank.
I consider it as a very secure way to log in.
>> If so, what a hassle if you don't have it on you.
That's correct. If you don't have it on you, you can't log in.
(What's the proglem? If you don't have your home key, you don't get in)
>> Sounds like a great way to turn people off internet banking.
It's ALWAYS a tradeoff between flexibility/usability and security.
If it is about banking stuff I prefer security and I am willing to give up some flexibility/usability.
Ah, now I understand. So, an electronic device that will only accept a valid card (maybe "any" valid card, and produces a unique one time use code.
Rabobank in NZ use that except it does not need the card. It relies on your inputting of account number/card number (can't remember which not my account) and then correct password before it will generate the one off code.
Agree with on on the trade off though. Better minor hassles than major ones.
I've been using Lastpass for several years, and can recommend it highly.
All of my passwords on web sites all over the world look like this one: rmmtHWGFdHMpQ$c!S66c I sometimes run into a problem where a site says that my password is too long!
And all I have to remember is the master password that unlocks the vault. For that one, I use an algorithm similar to the one that Rob suggests in this article.
Pain in the bum if you don't have the software with you though. And frankly, I don't trust anything that is stored in the cloud. No matter how secure they say it is. Look how safe everything was in Megaupload. Boom, taken down (allegedly illegally) and all the honest people lost their data. And wasn't Lastpass hacked recently?
>Pain in the bum if you don't have the software with you though.
Not at all. If I don't have the software with me and I need a password (when I'm on a friend's computer, perhaps), I can log in to my LastPass Vault securely and grab it from there. The local software is only for filling in forms automatically and synching with LastPass servers.
> And frankly, I don't trust anything that is stored in the cloud. No matter how secure they say it is.
You say you don't trust anything that is stored in the cloud, but you use a banking site. Do you honestly see a difference between the cloud and the internet?
LastPass uses AES-256 to calculate the encrypted passwords. If you think you can break that in finite time, I'll wager that you cannot. Your password is more likely to be stolen by a keylogger or through social means than cracking the algorithm mathematically. Your master password is only used locally; it is never sent to LastPass servers (if you forget your master password then they cannot tell you what it is - there is a recovery procedure but it's better to not forget)
>Look how safe everything was in Megaupload. Boom, taken down (allegedly illegally) and all the honest people lost their data.
You cannot compare LastPass with Megaupload - they are two very different services. If LastPass were to vanish overnight (or experiences downtime - unlikely with two data centres), I would still have all my passwords encrypted locally and available through the master key that only I know. I would not be able to add new sites, but I wouldn't lose access to any of the old ones.
>And wasn't Lastpass hacked recently?
No.
The New York Times published an article last year which included a statement by Paul Kocher that he wouldn't use password managers because he didn't want to lose his passwords if someone steals his computer. A security conference in Amsterdam last year included a paper by Andrey Belenko and Dmitry Sklyarov that pointed out weaknesses in *mobile* password managers such as those on iOS and Blackberry. No mention was made of Windows or Linux.
>Not at all. If I don't have the software with me and I need a password (when I'm on a friend's computer, perhaps), I can log in to my LastPass Vault securely and grab it from there. The local software is only for filling in forms automatically and synching with LastPass servers.
Point taken.
>You say you don't trust anything that is stored in the cloud, but you use a banking site. Do you honestly see a difference between the cloud and the internet?
Absolutely, while the cloud is on the internet it isn't the internet. Also, my bank, probably yours too, would reimburse me any losses due to fraudulent activity. BUT, that doesn't help with the mess to be cleaned up if that were to happen.
What would LastPass reimburse me if they got hacked and my details were compromised because of it? That's right, NADA.
>LastPass uses AES-256 to calculate the encrypted passwords. If you think you can break that in finite time, I'll wager that you cannot.
I'm not worried about what I can break/crack. I already know how awesome I am at that. NOT!
Your password is more likely to be stolen by a keylogger or through social means than cracking the algorithm mathematically. Your master password is only used locally; it is never sent to LastPass servers (if you forget your master password then they cannot tell you what it is - there is a recovery procedure but it's better to not forget)
>Look how safe everything was in Megaupload. Boom, taken down (allegedly illegally) and all the honest people lost their data.
>You cannot compare LastPass with Megaupload - they are two very different services. If LastPass were to vanish overnight (or experiences downtime - unlikely with two data centres), I would still have all my passwords encrypted locally and available through the master key that only I know. I would not be able to add new sites, but I wouldn't lose access to any of the old ones.
Sorry I disagree with you. Comparing LastPass and Megaupload is valid. While they are different services, they are (or were in the case of Megaupload) in the cloud. And LastPass could suddenly disappear for a whole host of different reasons. Likely? Yes. Soon? Probably no.
Whilst you may have access to your passwords locally, that is only as good as the data. What if it happened to get corrupted? Unlikely? Yes. Impossible? No. Don't argue, I have the infamous Mr Murphy and his law stuffing up my life on a regular basis.
>>And wasn't Lastpass hacked recently?
No.
The New York Times published an article last year which included a statement by Paul Kocher that he wouldn't use password managers because he didn't want to lose his passwords if someone steals his computer. A security conference in Amsterdam last year included a paper by Andrey Belenko and Dmitry Sklyarov that pointed out weaknesses in *mobile* password managers such as those on iOS and Blackberry. No mention was made of Windows or Linux.
Was unaware of that. Must have been published on that day that I slept in... LOL
I wasn't aware of that, MC. Thanks.
Reading through the CEOs interview, and seeing what's on the LastPass blog, I see nothing to convince me to stop using the service. My master password is strong, and I change it at random intervals.
Still, one can't say "LastPass was hacked recently". To be fair, this "possible hack" was more than two years ago.
Ah, someone who sees it as I do. Kudos to the Midnight Cowboy.
I second that!
Thanks for this article! Great way to make strong passwords.